 ≡
≡
This article covers all currently known free solutions for autologon and gives special attention to their levels of security and usability.
Registry
 The most widespread solution since the beginning of the Windows NT era in 1993 – modifying the registry –
has never changed. It is still free, simple, and absolutely insecure.
The most widespread solution since the beginning of the Windows NT era in 1993 – modifying the registry –
has never changed. It is still free, simple, and absolutely insecure.
Before giving instructions on how to apply this method, it is necessary to explain its disadvantages. The point is that in this case logon information (a user name and password) is stored in the system registry in plain text and accessible to anyone working on the computer. Administrative privileges are not needed to read the registry, so users and guests can easily retrieve this sensitive information (in most cases even remotely).
Also, it is not recommended to work with the registry unless you are completely sure you can do it right. Whenever technical advice from Microsoft requires modifications of the registry, they always put a warning like this: “This section, method, or task contains steps that tell you how to modify the registry. However, serious problems might occur if you modify the registry incorrectly. Therefore, make sure that you follow these steps carefully.” If you do not want to work with the registry directly, you can try one of the other solutions described in this article.
Instructions
- Start Registry Editor
(details) How to start Registry Editor in Windows 10/8/7/Vista and Windows Server 2019/2016/2012/2008
- Click Start, type regedit in the Start Search box, and then press ENTER.
- If you are prompted for a User Account Control confirmation, click Continue.
How to start Registry Editor in Windows NT4.0/2000/XP/Server 2003
- Click Start, and then click Run.
- Type regedit in the Open box, and then click OK.
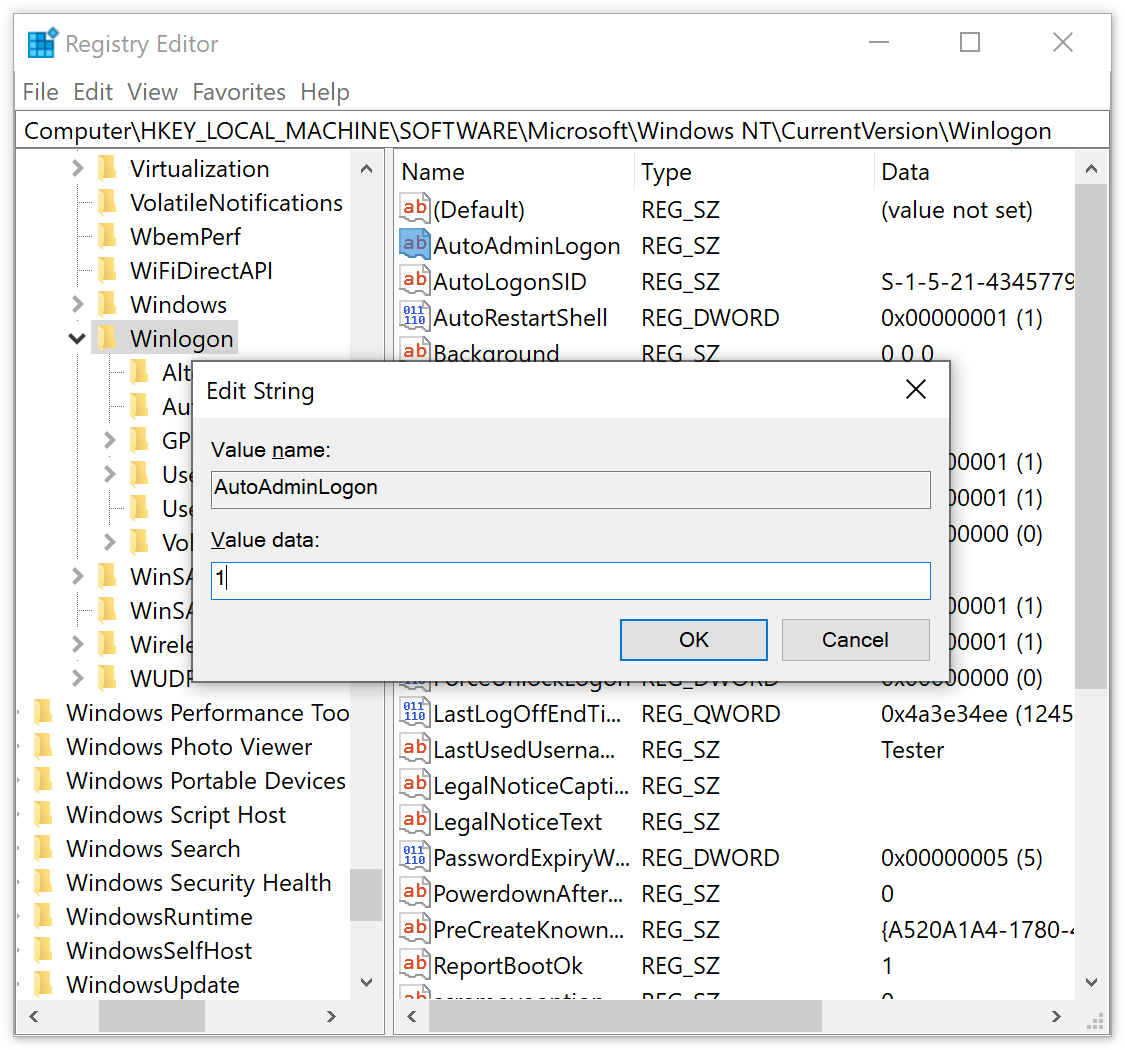
- Navigate to the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon -
Add the values with the corresponding data from the table below to the selected Winlogon key.
If these values already exist there, just edit them
(details) How to add a string value to a registry key
- Right-click the key, choose New, and then click String Value.
- Type a name for the new value, and then press ENTER.
How to edit a string value
- Click a registry key to display its values, and then double-click the value that you want to edit.
- Type some text in the Value data box, and then click OK.
The ForceAutoLogon value should be added to the Winlogon key only if the computer is running Windows 2000.Value Name Value Data AutoAdminLogon 1 DefaultUserName A user name to be used for automatic logon DefaultPassword The password for the user name ForceAutoLogon 1 - On the File menu, click Exit to close Registry Editor.
Advanced User Accounts Control Panel
 The second method has, in essence, the same principle as the previous one: logon credentials are stored in
the system registry in plain text. The difference here is that you use the built-in capabilities of the
operating system instead of having to deal with the registry directly.
The second method has, in essence, the same principle as the previous one: logon credentials are stored in
the system registry in plain text. The difference here is that you use the built-in capabilities of the
operating system instead of having to deal with the registry directly.
This solution also does not provide any security at all, because attackers can easily get your user name and password from the registry both locally and remotely.
In addition, this method will not work if the computer is a member of an Active Directory domain.
Instructions
- Start Advanced User Accounts Control Panel
(details) How to start Registry Editor in Windows 10/8/7/Vista and Windows Server 2019/2016/2012/2008
- Click Start, type control userpasswords2 or netplwiz in the Start Search box, and then press ENTER.
- If you are prompted for a User Account Control confirmation, click Continue.
How to start Advanced User Accounts Control Panel in Windows 2000/XP/Server 2003
- Click Start, and then click Run.
- Type control userpasswords2 (control userpasswords in Windows 2000) in the Open box, and then click OK.
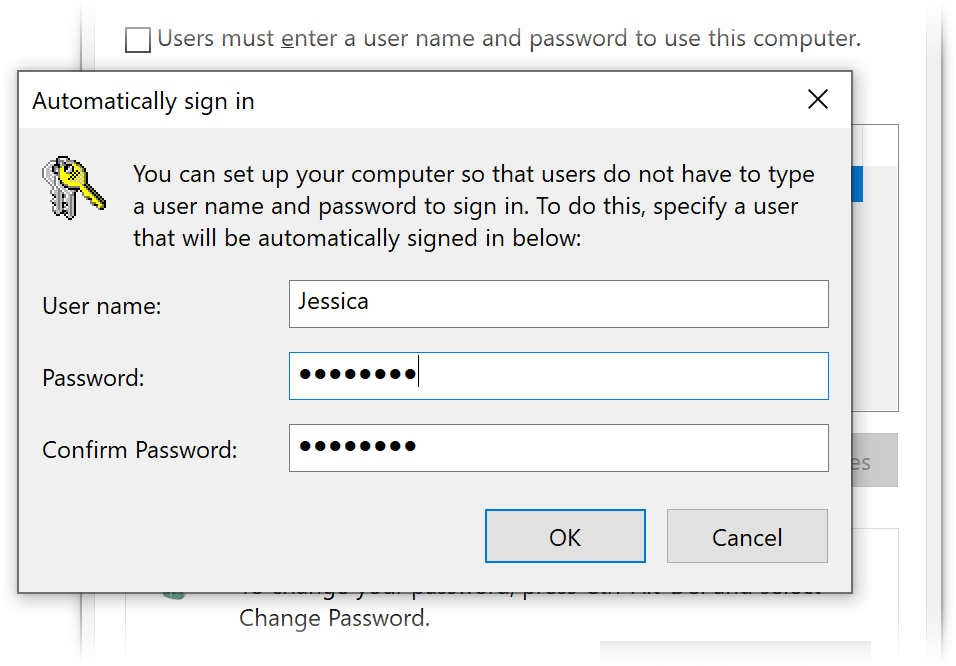
- In the User Accounts (Users and Passwords in Windows 2000) dialog box, on the Users tab, click to clear the Users must enter a user name and password to use this computer check box, and then click OK.
- In the Automatically Log On dialog box, type a user name and password to be used for auto login in the User name and Password boxes respectively, type the password again in the Confirm Password box, and then click OK.
- Click OK to close the User Accounts (Users and Passwords in Windows 2000) dialog box.
LSASecret
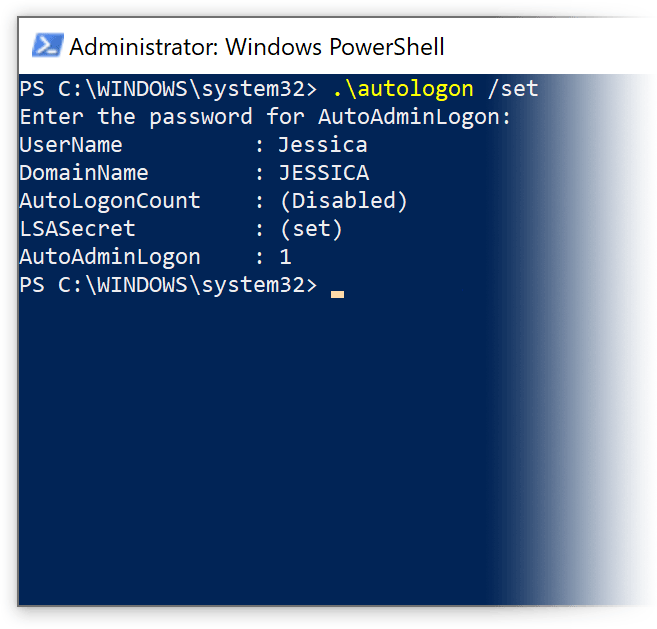 In October 2006 Microsoft professionals from Shell: Revealed created a new solution known as autologon.exe.
This is an application that stores logon data in LSASecret.
The tool is not supported officially, works only on Windows Vista and Windows 2008, and has a rather unfriendly command line interface.
The autologon.exe related blog entry is now accessible only via the Internet Archive’s
Wayback Machine,
since the Shell: Revealed website has not worked for quite a while and no one knows if it will ever be relaunched.
In October 2006 Microsoft professionals from Shell: Revealed created a new solution known as autologon.exe.
This is an application that stores logon data in LSASecret.
The tool is not supported officially, works only on Windows Vista and Windows 2008, and has a rather unfriendly command line interface.
The autologon.exe related blog entry is now accessible only via the Internet Archive’s
Wayback Machine,
since the Shell: Revealed website has not worked for quite a while and no one knows if it will ever be relaunched.
In November 2006 Mark Russinovich of Sysinternals updated his Autologon for Windows that had employed the registry before. This tool supports Windows XP and higher. The author does not specify the place used now for storing logon information, but a quick search finds an almost complete source code for his application on Microsoft Developer Network which tells us it is LSASecret too.
Thus, we seem to have finally got a secure place to keep logon credentials, but the fact is your user name and password are again stored in the system registry, since LSASecret is a hidden part of it. The credentials are not encrypted, they are just hidden. As compared to the solutions mentioned earlier, it is a bit harder for intruders to get to your logon data in this case, but they still can do it by applying, for example, LSASecretsView tool. This simple utility is available on the developer’s webpage.
Tweakers
Tweaking applications are those designed to give access to settings that are not exposed in the operating system. The first program of this kind is presumed to be Tweak UI from Microsoft which appeared in the middle of the 1990s and has had many clones ever since. Some of them are freeware, but for most you will have to pay. Among plenty of features tweakers provide they usually have an ability to perform automatic logon, but again there is nothing new here – they place your logon name and password into the registry.
Other Third-Party Tools
There are a lot of other free third-party solutions for autologon, but you should keep in mind that all of them use the registry for storing login information in plain text. Moreover, most commercial solutions follow the same insecure principle.